It’s increasingly important to understand attacks on your personal information and the potential impact on your financial health.
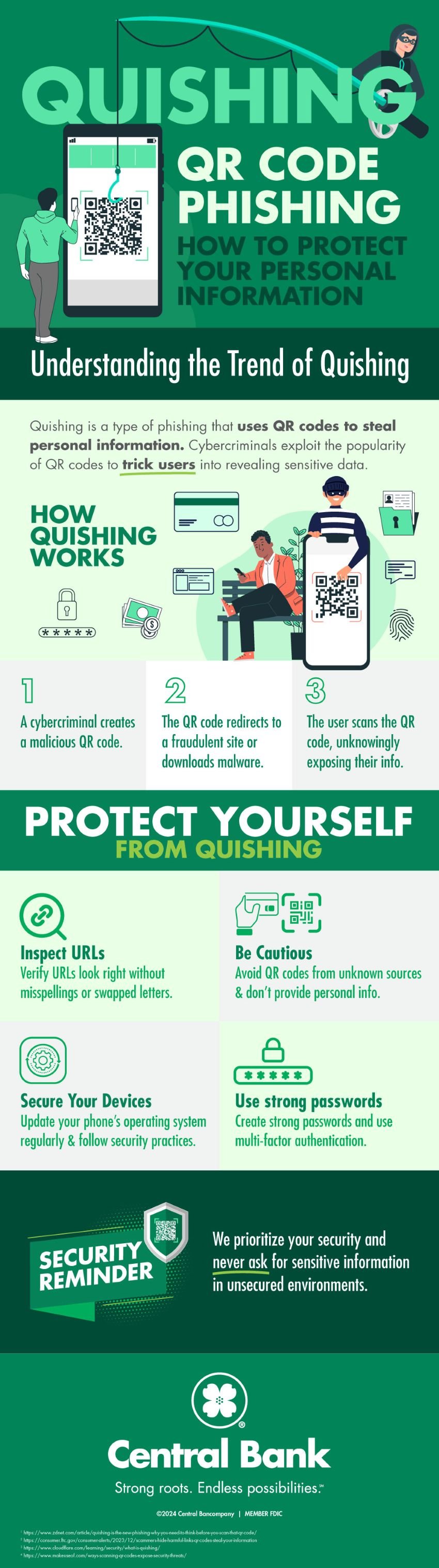
A relatively new and growing threat is called quishing. Most of us by now are familiar with the term phishing when it comes to cyber-attacks, typically in the form of phishing emails. Quishing is a type of phishing that involves QR codes. With the popularity and convenience of scanning QR codes to access information, it was inevitable that cyber criminals would find a way to fraudulently gain access to personal information through this technology.
This trend has become enough of a threat that late last year the Federal Trade Commission (FTC) released an alert warning consumers to be on the lookout for harmful links hidden in what may seem like safe QR codes.
In short, the FTC provides the following guidance to protect yourself from quishing attacks:
- If you see a QR code in an unexpected place, inspect the URL before you open it. If it looks like a URL you recognize, make sure it’s not spoofed — look for misspellings or a switched letter.
- Don’t scan a QR code in an email or text message you weren’t expecting — especially if it urges you to act immediately. If you think the message is legitimate, use a phone number or website you know is real to contact the company.
- Protect your phone and accounts. Update your phone's OS to protect against hackers and protect your online accounts with strong passwords and multi-factor authentication.
Understanding Phishing and How It Has Evolved
Phishing is a common method cybercriminals use to access valuable data, typically financial in nature, primarily through email attacks. Often, a phishing email contains a link or attachment with an aim of getting the targeted user to click the link that takes the victim to a malicious website, or to download the attachment. This will then lead to the fraudster stealing sensitive information, such as login credentials for online accounts, financial information or other personal data.
Because cybercriminals are always evolving their tactics as cybersecurity and cyber education improves, new phishing strategies have emerged, such as vishing (voice phishing), smishing (SMS phishing), and quishing (QR phishing). These new variations are leveraging additional communication channels to carry out similar deceptive practices.
Quishing Tactics Used by Bad Actors: Spoofed Sites, Information Theft and Malware
A quishing attack starts with a cybercriminal creating a QR code that redirects a target to a fraudulent login page in order to dupe the target into providing credentials or redirecting to a site that automatically downloads malware upon scanning.
What is a QR Code and What Are Some of Its Problems?
Quick Response codes, or QR codes for short, are barcodes that can easily be scanned with a camera or a code reader application. The main reason for their popularity is that QR codes can store significant amounts of information helpful to consumers, such as website URLs, product details, or contact information. Scanning technology has made it very easy to use smartphone cameras or code readers to access the website to which the URL points.
The benefits of QR codes are also some of their biggest challenges: their incredible convenience, their familiarity - and therefore trust - among users, the amount of data they can contain, and their ability to give up your location data.
Why the Rising Use of Mobile Phones is Important
A victim’s unintentional cooperation is important for a successful phishing attack, so it only makes sense that the factor that has had the most impact in its evolution is the prevalence of mobile phones among users. Because mobile devices are often used “on the go,” potential victims are often not paying close attention to suspicious communications, links and attachments, making them more vulnerable to cybercriminals.
Protective Measures Against Quishing
In short, use the same care as you would to protect yourself from any type of online fraud. Make sure to verify the URL associated with the code, and refrain from submitting personal information, making payments, or downloading anything from a site assessed through a QR code. It’s also critically important to make your device security updates, utilize strong passwords, and use multifactor authentication. By adopting these practices, individuals can reduce the risk of falling victim to quishing attacks.
At Central Bank, we take your security very seriously and are here to help. Always know that there are certain sensitive information that we will not ask for in a non-security environment.